Unified, Exposed and Everywhere: Why Mobile, API & Cloud Must Be Secured Holistically
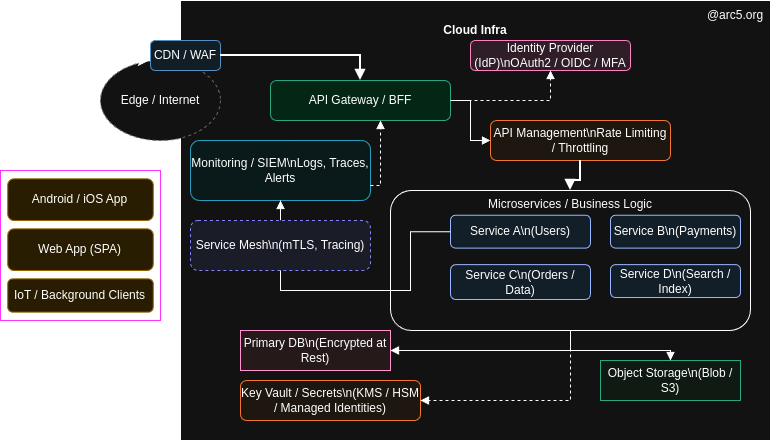
In modern system architectures, mobile apps, backend APIs, and cloud services form a single interconnected ecosystem – a labyrinth of services and data flows. Mobile clients talk to APIs which in turn manipulate cloud resources, and each component is exposed to the Internet. This means attackers anywhere in the world can traverse from a compromised phone to your APIs and into your cloud. In fact, insecure APIs are now the top risk in mobile apps; the OWASP Mobile Top 10 (2024) calls out “insecure API and communication” as the #1 danger. A few sloppy secrets or validation checks in this chain, and an attacker can slip through.
One mis-typed header or open port in any corner of the maze can invalidate defenses everywhere. For example, a flawed Azure Logic App connector (part of Azure’s API management infrastructure) allowed a researcher with only Contributor-level access to hijack any API Connection globally - gaining administrator privileges on downstream resources (Azure Key Vaults, SQL databases, even third-party services like Jira or Salesforce) across all tenants. In short, a single vulnerability exposed everything. Similarly, an Azure Entra ID (Azure AD) token validation bug (CVE-2025-55241) let attackers impersonate any user, even Global Admins in any tenant, effectively handing over the keys to all Azure resources. As Microsoft noted, such a flaw could grant “full tenant compromise” with access to every service in that tenant. These case studies show that any weak link - mobile, API, or cloud can lead to a complete breach.
Threats Everywhere: Real-World Case Studies
-
Azure API Management (APIM) – SSRF & Path-Bypass (2023): Security research showed that even managed API gateways can be flawed. Tenable reported server-side request forgery and file upload path-traversal bugs in Azure’s API Management (APIM) service. Although Microsoft quickly patched them, it highlights how an attacker could use a proxy service to reach internal endpoints if left open.
-
Azure Logic Apps - Cross-Tenant API Connections (2025): A critical flaw was found in Azure’s shared API Connection infrastructure (part of Logic Apps). Researchers demonstrated that by calling an undocumented ARM endpoint, an attacker could traverse the path parameters (e.g. using “../../”) and then hijack any API Connection across all tenants, with full backend privileges. In effect, one would gain admin-level access to victim Key Vault secrets, SQL databases, and linked services.
-
Azure Entra ID (AD) - Global Admin Impersonation (2025, CVE-2025-55241): In July 2025 Microsoft patched a bug in the legacy Azure AD Graph API. This “actor token” flaw let an attacker present a token from their own tenant and impersonate any user (including Global Admins) in another tenant. Under this exploit, the attacker could create accounts, grant themselves roles, and take control of all tenant resources (SharePoint, Exchange, Azure subscriptions, etc.) without triggering conditional-access or MFA.
-
Public API Breaches (2024): Insecure APIs have led to massive data leaks. For instance, attackers exploited multiple critical bugs in an e-commerce API (PandaBuy) to exfiltrate 1.3 million user records.
-
In another incident, an exposed partner-portal API in a large tech company (Dell) allowed thieves to siphon 49 million customer records. Even widely-used services weren’t spared: a weakness in Trello’s API enabled linking of private emails to accounts, compromising 15 million users. Such breaches underscore that a vulnerability in an API (or its credentials) can spill out user data on a colossal scale, this data possibly residing on Cloud
These examples make the point: you cannot secure mobile, API, or cloud in isolation. A flaw in any part of the chain becomes a backdoor to the whole. As one security researcher warned, “API Connections allow anyone to fully compromise any other connection worldwide”, and compromised tokens or secrets often mean “full access to any resource hosted in Azure”
Securing the Ecosystem: A Holistic Approach
To break this vicious cycle, organizations must secure the entire stack, end-to-end, not piecewise. It’s not enough to protect only the cloud or only the mobile client. The following best practices apply.
1. Design for the Full Path:
Model the data flow from mobile to API to cloud. Treat each API call as running in a hostile environment. Apply principle-of-least-privilege everywhere. For example, do not allow an API token scoped for a single microservice to access unrelated resources. Studies have found that overwrought trust in headers or tokens was exactly what allowed Azure’s API and AD exploits.
2. Harden Mobile Clients:
Mobile apps should avoid hard-coded keys. Use strong attestation (certificate pinning, protected storage). Never trust data coming from the client. Use robust API authentication (OAuth tokens bound to the app and user). Remember that stolen or leaked mobile credentials become literal keys to your APIs.
3. Protect the APIs:
Implement strong authentication and input validation on all APIs. Use rate-limiting, anomaly detection, and API gateways or WAFs to watch for abuse. Follow the OWASP API Security Top 10 (2023) – e.g. enforce TLS everywhere, rotate secrets, log and revoke compromised tokens. As highlighted by recent breaches, insecure API secrets are a critical risk.
4. Secure the Cloud Infrastructure:
On the cloud side, enforce Conditional Access, MFA, and just-in-time elevation. Monitor service principals and remove legacy (e.g. Azure AD Graph) endpoints promptly. Keep cloud service updates current. For example, Microsoft had to deprecate an old Graph API after these attacks. Use cloud-native security features (like Azure Defender, AWS GuardDuty) to spot lateral movement or unusual API usage.
5. End-to-End Testing and Monitoring:
Continuously pen-test the entire workflow - from mobile UI through to backend logic. Validate that API fixes cannot be bypassed (e.g. replay or smuggling attacks in proxies, as seen with HTTP request smuggling in ASP.NET Core). Centralize logs across mobile, API gateway, and cloud, so an intrusion anywhere triggers alerts everywhere.
In Summary
The only real path forward is holistic security. Think in ecosystems, not components. Apply Defense-in-Depth. Embrace Zero-Trust. Securing the mobile app while leaving its APIs exposed, or hardening the APIs while the cloud infrastructure gapes open elsewhere, is an illusion of safety. A single unlocked corridor compromises the entire castle.
When we treat the mobile client, the APIs that feed it, and the cloud that powers it as one inseparable system, we seal every approach an attacker might take. We deliver an environment where no single flaw can topple the whole stack.
This end-to-end mindset -from client to cloud - is the only sustainable path to trust and resilience in a world where everything is unified, everything is exposed, and everything is everywhere.
References
- https://nvd.nist.gov/vuln/detail/CVE-2025-53767?utm_source=chatgpt.com "NVD - CVE-2025-53767"
- https://www.incibe.es/en/incibe-cert/early-warning/vulnerabilities/cve-2025-53767?utm_source=chatgpt.com "CVE-2025-53767 | INCIBE-CERT | INCIBE"
- https://nvd.nist.gov/vuln/detail/CVE-2025-29827?utm_source=chatgpt.com "NVD - CVE-2025-29827"
- https://karl.fail/vulnerabilities/vulnerabilities-cve-2025-29827/?utm_source=chatgpt.com "CVE-2025-29827: Critical Privilege Escalation in Azure Automation - Karl.Fail"
- https://www.ameeba.com/blog/cve-2025-29827-critical-privilege-escalation-vulnerability-in-azure-automation/?utm_source=chatgpt.com "CVE-2025-29827: Critical Privilege Escalation Vulnerability in Azure Automation - Ameeba Exploit Tracker"
- https://insights.integrity360.com/threat-advisories/microsoft-patches-critical-entra-id-flaw-enabling-global-admin-impersonation-across-tenants?hs_amp=true&utm_source=chatgpt.com "Microsoft patches critical Entra ID flaw enabling Global Admin impersonation across tenants"
- https://www.cybermaxx.com/resources/critical-entra-id-vulnerability-cve-2025-55241-microsoft-issues-emergency-fix-for-cross-tenant-token-exploit/?utm_source=chatgpt.com "Critical Entra ID Vulnerability CVE-2025-55241: Microsoft Issues Emergency Fix for Cross-Tenant Token Exploit | CyberMaxx"
- https://securityonline.info/cve-2025-55241-microsoft-entra-id-flaw-with-cvss-10-0-could-have-compromised-every-tenant-worldwide/?utm_source=chatgpt.com "CVE-2025-55241: Microsoft Entra ID Flaw with CVSS 10.0 Could Have Compromised Every Tenant Worldwide"
- https://arxiv.org/abs/2509.10540?utm_source=chatgpt.com "EchoLeak: The First Real-World Zero-Click Prompt Injection Exploit in a Production LLM System"